- OpenSSL 1.0.2 ClientHello sigalgs DoS (CVE-2015-0291) - Severity: High
- Reclassified: RSA silently downgrades to EXPORT_RSA [Client] (CVE-2015-0204) - Severity: High
- Multiblock corrupted pointer (CVE-2015-0290) - Severity: Moderate
- Segmentation fault in DTLSv1_listen (CVE-2015-0207) - Severity: Moderate
- Segmentation fault in ASN1_TYPE_cmp (CVE-2015-0286) - Severity: Moderate
- Segmentation fault for invalid PSS parameters (CVE-2015-0208) - Severity: Moderate
- ASN.1 structure reuse memory corruption (CVE-2015-0287) - Severity: Moderate
- PKCS7 NULL pointer dereferences (CVE-2015-0289) - Severity: Moderate
- Base64 decode (CVE-2015-0292) - Severity: Moderate
- DoS via reachable assert in SSLv2 servers (CVE-2015-0293) - Severity: Moderate
- Empty CKE with client auth and DHE (CVE-2015-1787) - Severity: Moderate
- Handshake with unseeded PRNG (CVE-2015-0285) - Severity: Low
- Use After Free following d2i_ECPrivatekey error (CVE-2015-0209) Severity: Low
- X509_to_X509_REQ NULL pointer deref (CVE-2015-0288) Severity: Low
How bad will this actually be?
It is not bad as the heartbleed openssl bug disclosed in April 2014 in the OpenSSL cryptography library. But, new bug can cause "Denial of Service" and crash your services. It is good security practice, to quickly apply the patched version on your system and restart the affected services.How to find openssl version on a Linux?
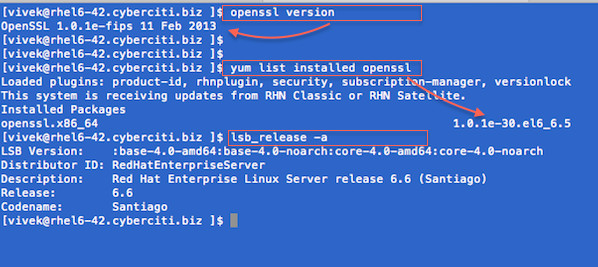
The syntax is as follows:Find openssl version on a CentOS/RHEL/SL/Fedora Linux
openssl version ## or ## sudo yum list installed opensslSample outputs:
A list of affected Linux distros
I recommend that you upgrade your openssl packages ASAP to avoid any security issues on both client and server systems powered by Linux based distro.- RHEL version 6.x
- RHEL version 7.x
- CentoS Linux version 6.x
- CentoS Linux version 7.x
- Debian Linux stable (wheezy) 7.x
- Ubuntu Linux 14.10
- Ubuntu Linux 14.04 LTS
- Ubuntu Linux 12.04 LTS
- Ubuntu Linux 10.04 LTS
How to patch on a Linux?
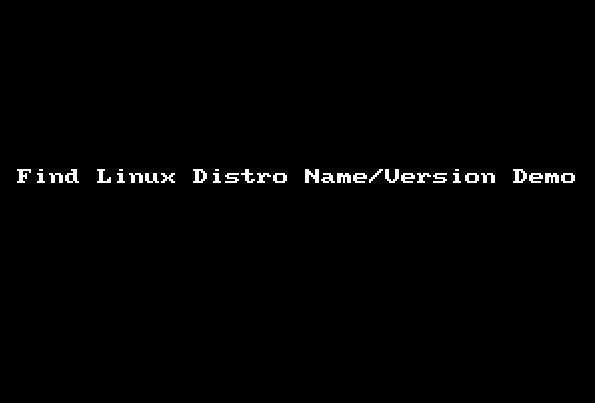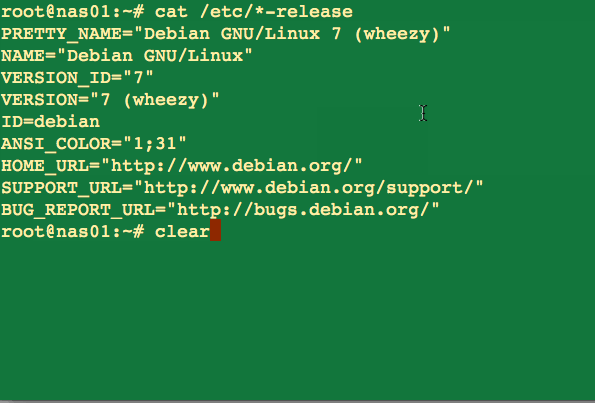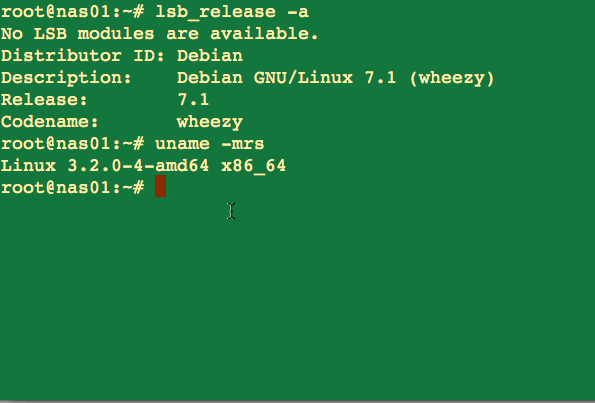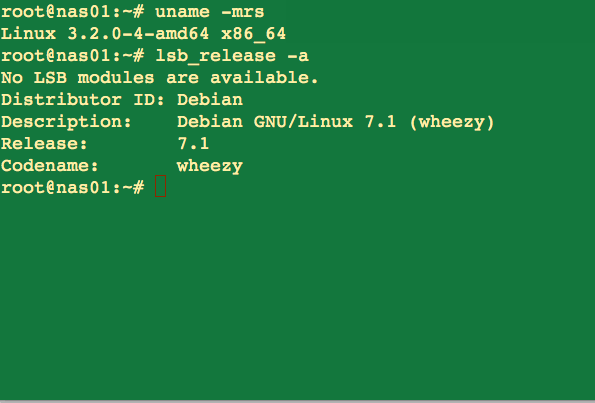
Type the following commands as per your distro version/type:## how do I find out my distro version? ## lsb_release -a ## or use ## cat /etc/*-releaseSample outputs:
CentOS/RHEL/Fedora Linux
Type the following yum command to patch openssl as root user to patch openssl:sudo yum clean all
To install the updates, use the yum command as follows:sudo yum update
To only update the OpenSSL package and its dependencies, use the following yum command:sudo yum update openssl
Debian/Ubuntu Linux
Type the following apt-get commands to patch openssl as root user to patch openssl:sudo apt-get update sudo apt-get upgradeSample outputs:
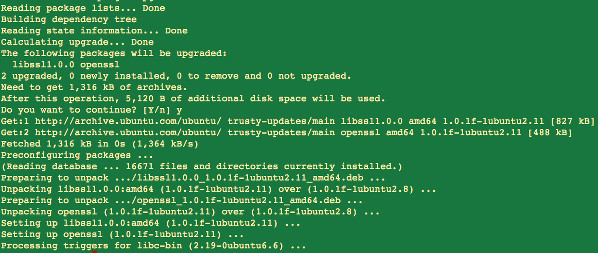
Fig.04: OpenSSL patched on a Ubuntu Linux
Do I need to reboot my server/laptop/computer powered by Linux?
Short answer - yes, you need to reboot your computer/server to make all the necessary changes. Sysadmin should plan on updating as soon as possible or use maintenance reboot window:sudo reboot
Long
answer - It depends. You can avoid reboot by restarting required
services. Fist, find all services that depend on the OpenSSL libraries,
and restart them one-by-one using the service command:### Debian/Ubuntu find out if service needed reboot ## checkrestart -v ## Generic method ## lsof | grep libssl | awk '{print $1}' | sort | uniqSample outputs:
hhvm mysqld nginx php5-fpmRestart the above services one-by-one, run:
sudo service restart hhvm restart sudo service restart mysqld restart sudo service restart nginx restart sudo service restart php5-fpm restart