To create a new policy in your Juniper SSG Firewall for blocking IP addresses, please follow these steps:
1. Log into the firewall. You will have been given an IP address and access to this IP address by support.
2. Once logged into the firewall, navigate to Policy on the left hand navigation bar. Expand Policy and click Policies Elements. Then expand Addresses and click List.

3. To add a new IP address, choose the source zone (typically Untrust) from the drop down at the top of the screen. Then click New.
4. In the Address Name field, enter in the IP address or host or host you wish to block. This can be in CIDR format. For the comment, we typically recommend putting "Blocked IP" although it's just for tracking purposes. Select the appropriate radio button (IP Address/Netmask or Domain Name) and enter in the information again. Leave the zone as Untrust and click OK.
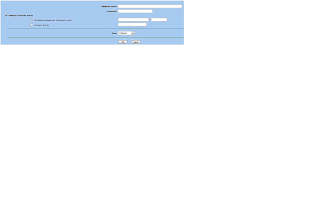
5. If you are adding multiple IP addresses to a blocked list, then it is recommended to create a group. Go back to Policy > Policy Elements > Addresses > Group > and add a new group. Name the group Blocked IP Addresses or something similar, and move the IP addresses/hosts from the left box to the right box and click OK.
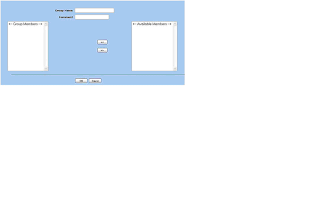
6. Now to add the policy. Navigate to Policy > Policies and choose the source zone (typically Untrust) and the destination zone (typically Trust) from the drop downs at the top of the screen. Then click New.
7. From the Source Address drop down, choose the source IP address or host. If this policy is for multiple sources, click the Multiple button and add the multiple sources from the list. From the Destination Address drop down, choose the destination IP address or host. If this policy is for multiple destinations, click the Multiple button and add the multiple destinations from the list. If you do not see your source or destination IP or host listed, make sure it exists under the zone under Policy > Policy Elements > Addresses > List. If it does not exist, add the IP or host under the appropriate zone.
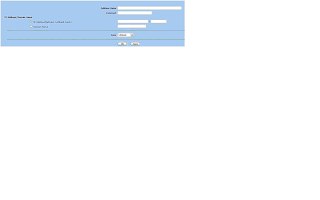
8. Under the Service drop down, select the service you will be connecting to. If you do not see the service listed, make sure it exists under the zone under Policy > Policy Elements > Services > Predefined. If it does not exist, click Custom and add the service ports (UDP, TCP, ICMP, or other).
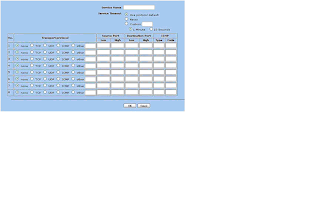
9. From the Action drop down, choose Deny. This will deny the policy.
10. If you wish to enable logging for the policy, check the box for Logging and at Session Beginning. Once the policy is to your liking, click OK and the policy has been added at the bottom of the listing for that interface group.
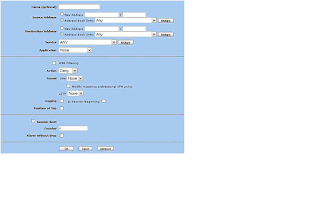
11. The main policy listing will show a red X under the Action column showing that the policy is denying traffic rather than showing a green checkmark for allowing traffic.
Note: Please do not modify the Global Policy section. Often times modifying the policies contained within will prevent our internal servers from communicating with your servers which includes monitoring services. Please check with support if you have questions before modifying these policies.



